Network PT Machines Writeups
Hello, I am Caesar3 and today this is my writeups for both Network PT Machines provided by CyberHub & Flagyard.
First Machine:
after importing machines to vmware we have to power the first machine on.

Now lets get started:
recon:

first with nmap to find the IP of the machine after getting the subnet above using ifconfig.

but lets check the machine mac address to find the right ip address using settings -> Network Adapter -> advanced and we have the mac address.

so the ip for the machine is 192.168.142.131.
and now nmap it:
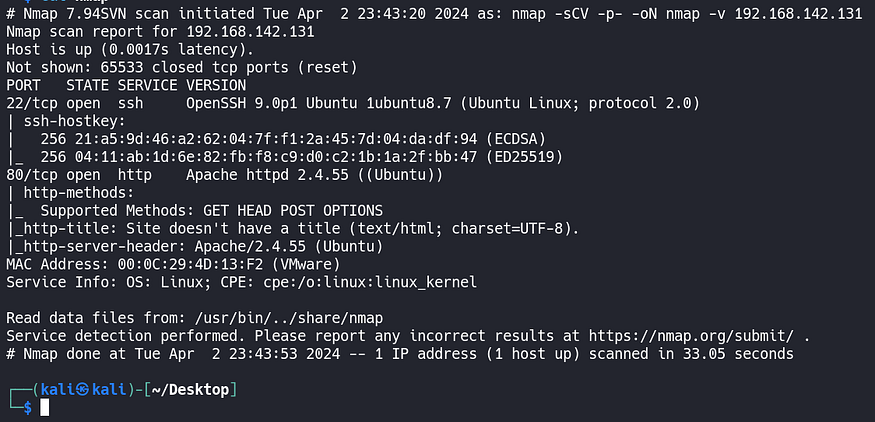
we have a web page running on apache, and ssh on port 22.
exploit:

as we see above if g and p are not empty we call g on p, so lets call system function from php on what we input for p:
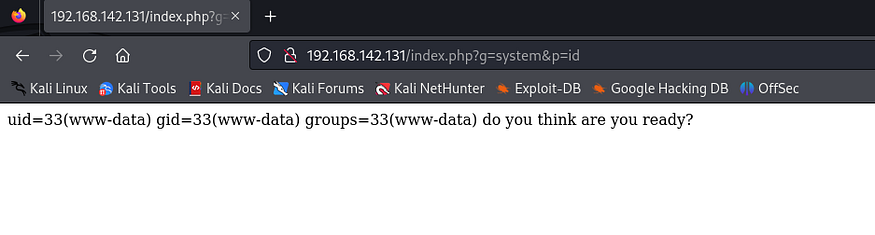
we have command injection, cat /etc/passwd we find a user that is not a system or service user which is auditor.

for now I’ll try to brute force the user maybe we’ll get a password.
and luckily we got one:

after logining in and ls the home directory we got the user.txt flag:
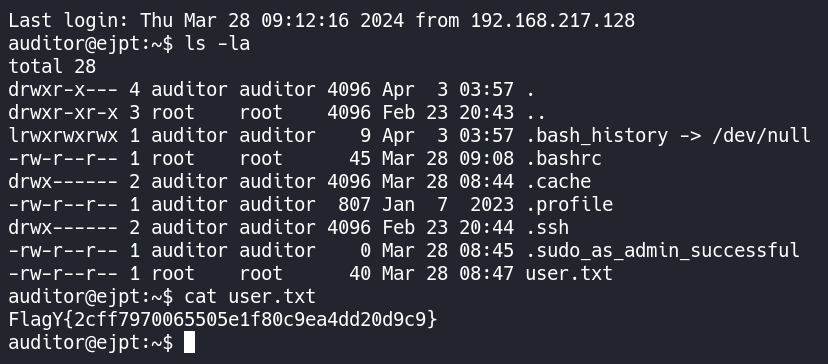
privesc:
if we do sudo -l we’ll see that we can find binary with sudo privileges without password:

so using gtfobins to try to find a sudo command with find to escalate our privileges to root:

and finally we got the root.txt flag:

Second Machine:
after importing the machine, like what we did previously, and ip for this machine is 192.168.142.133.
recon:
namp result we have apache server running on port 80 and ssh on port 22:

exploit:
opening the web page:

after trying to find a vulnerability I found command injection in action parameter:

find if we have python3 on the server:

and yes we have python3, using revshells website we got a python script that gives us a reverse shell:

I gave it my IP and port I wanted, and here we have our python but before, we have to set a netcat listener on the same port to get the reverse shell.

getting a reverse shell:
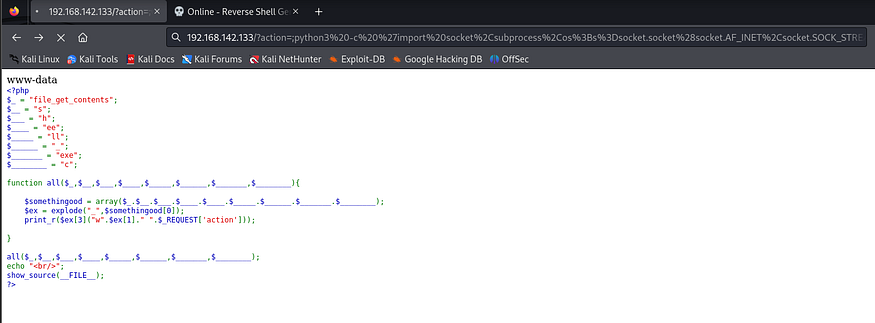

and here we go, lets make it interactive shell:

here we have creds for the user john:

I moved to /home directory, and switch user to john, and maybe we have restricted shell for some command, but we got the user.txt flag:

privesc:
here we can run this php script with sudo:

lets find out how can we escalate our privileges using this script, so we read it:
as we see above that we have to put f and set a function as option in our sudo command and empty -h option it will copy find binary to tmp with what we specified for f option for example exec, and it will make it suid binary, so we can run it as root without password. lets check it out:

it prints Impelented Done which sounds good but also lets check our /tmp directory:

and yes the command has executed, and we have system (which is find binary) with suid permissions, so now we can use our previous privilege escalation technique but with some changes, but we should remember that johns’ shell has some restricted command so we switch again to www-data to avoid the restrictions and execute it:

we added -p to be root, or we just can do ./system . -exec cat /root/root.txt \; -quit to read it, and here we have the root.txt flag.
Thanks.
Last updated